The Article Tells The Story of:
- A critical SonicWall firewall vulnerability (CVE-2024-53704) allows hackers to hijack VPN sessions.
- Attackers can bypass authentication and access private network resources using a crafted session cookie.
- Administrators must update affected devices immediately to prevent exploitation.
Critical SonicWall Firewall
Security researchers have uncovered a critical vulnerability in SonicWall firewalls that allows hackers to hijack active VPN sessions. The flaw, identified as CVE-2024-53704, bypasses authentication mechanisms in certain versions of the SonicOS SSLVPN application. This vulnerability poses a significant risk, enabling attackers to gain unauthorized access to private networks. SonicWall has urged administrators to update their firmware immediately to mitigate the threat.
Check Out Latest Article Of Microsoft Warns: Hackers Exploit ASP.NET Keys to Hijack Servers—Is Your Data at Risk? Published on February 8, 2025 SquaredTech
How the Exploit Works
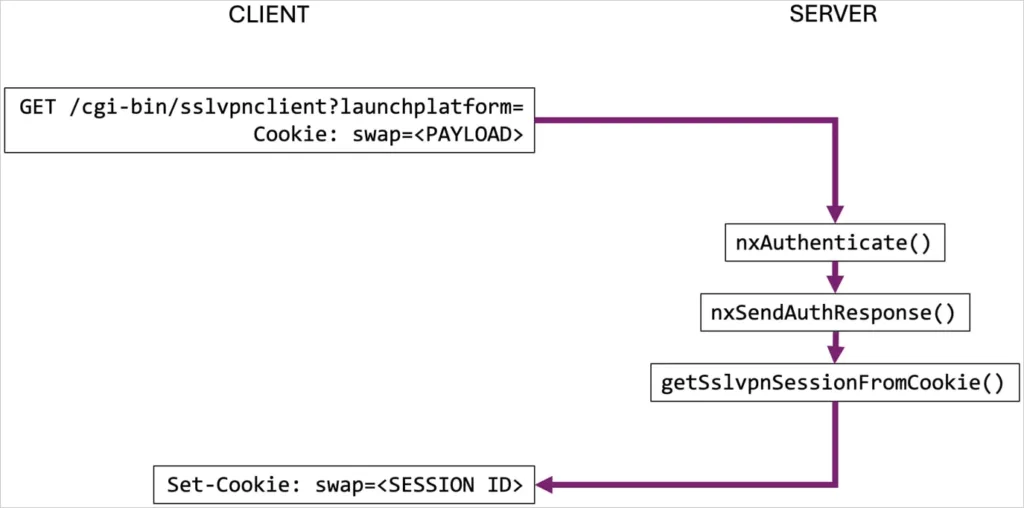
The vulnerability exploits a flaw in the SSL VPN authentication process. Attackers can send a specially crafted session cookie containing a base64-encoded string of null bytes to the SSL VPN authentication endpoint at ‘/cgi-bin/sslvpnclient.’ This triggers an incorrect validation of the session, logging out the legitimate user and granting the attacker access to the VPN session.
Once inside, the attacker can read the user’s Virtual Office bookmarks, obtain VPN client configuration settings, open a VPN tunnel to the internal network, and access private network resources. Researchers at Bishop Fox confirmed the exploit’s effectiveness by creating a proof-of-concept code that successfully hijacked an active session.
Affected Devices and Firmware Updates
The vulnerability impacts SonicOS versions 7.1.x (up to 7.1.1-7058), 7.1.2-7019, and 8.0.0-8035. These versions run on multiple models of Gen 6 and Gen 7 firewalls, as well as SOHO series devices.
SonicWall has released security updates to address the issue. Patched versions include SonicOS 8.0.0-8037 and later, 7.0.1-5165 and higher, 7.1.3-7015 and higher, and 6.5.5.1-6n and higher. Administrators should check SonicWall’s official bulletin for model-specific update instructions.
Immediate Action Required
As of February 7, internet scans revealed approximately 4,500 SonicWall SSL VPN servers exposed online without the necessary security updates. With the proof-of-concept exploit now publicly available, the risk of exploitation has increased significantly.
Bishop Fox researchers emphasized the urgency of applying the updates. Delaying the patch could leave networks vulnerable to attacks, potentially resulting in data breaches, unauthorized access, and other security incidents.\
Stay Updated: Tech News


