The Article Tells The Story of:
- Hackers Send Fake Emails Using Google’s Own Authentication: Attackers trick users with DKIM-signed messages that look official.
- Fraudulent Support Portals Collect Logins on Google Domains: Phishing pages hosted on Google Sites appear genuine to most users.
- Google and PayPal Vulnerabilities Exploited in Similar Attacks: OAuth and system alerts are used to deliver fake messages that pass security checks.
Fake Google Emails Pass All Security Checks in New Phishing Attack
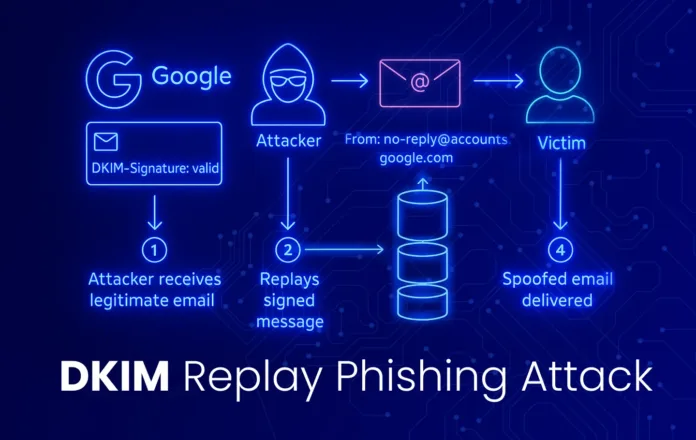
Hackers abuse Google OAuth to spoof Google in DKIM replay attack, sending emails that appear to come from Google’s official address. These messages pass DKIM verification and look completely legitimate. But instead of helping users, they lead to fake websites designed to steal Google account credentials.
The phishing emails arrive from no-reply@google.com. They pass all authentication checks, including DomainKeys Identified Mail (DKIM), and land in inboxes next to real Google alerts. This gives them a sense of authenticity. The goal is to trick users into visiting a fake support portal that looks like a real Google site.
Security expert Nick Johnson, developer of Ethereum Name Service (ENS), discovered the attack after receiving a fake alert about a legal subpoena. The message passed DKIM checks, mimicked Google’s formatting, and was hosted on a legitimate Google domain. But the link led to a fraudulent support page.
This new method targets even tech-savvy users by exploiting Google’s own email and OAuth systems.
Fake Support Portals Hosted on Google Sites Steal Logins
The phishing email led Johnson to a page hosted on sites.google.com, Google’s free website builder. At first glance, the site looked like a standard Google support page. It asked for login details and showed no obvious signs of fraud.
But Johnson noticed the address was not accounts.google.com, which is the real login domain for Google services. That small detail exposed the fraud. Johnson called the fake site an “exact copy” of the real portal, with the only difference being the domain name.
Because the page was hosted on a trusted Google domain, most users wouldn’t think twice before entering their credentials.
The real trick, though, was how the attacker made the email pass Google’s DKIM check. This made the message appear genuine in Gmail and other email platforms.
How Hackers Abuse Google OAuth to Spoof Google in DKIM Replay Attack
Johnson analyzed the process step-by-step and revealed how attackers exploited Google’s systems:
- Register a Fake Domain: The attacker sets up a domain and creates a Google account using an address like me@[fake-domain].
- Create a Malicious OAuth App: The attacker creates an app in Google’s OAuth system and names the app using the entire phishing message, including blank spaces to hide content.
- Trigger a Real Google Security Alert: By giving the app access to their email account, Google automatically sends a security email to the attacker’s inbox.
- Forward the Google-Generated Alert to Victims: Because Google created the email, it comes with a valid DKIM signature. The attacker forwards this alert to their targets.
This process allows attackers to send emails that appear to be signed and delivered by Google. Gmail and other systems treat these messages as safe because the DKIM signature is valid.
Gmail also displays the recipient as if it matches the victim’s address. That’s because the attacker used the “me@” email format, which tricks Gmail’s visual formatting. All of these details combine to make the email seem 100% real.
Security company EasyDMARC also examined the attack and confirmed that it exploits weaknesses in DKIM verification. The DKIM system checks only the message body and specific headers—not the full envelope of the email—allowing the fake to pass as real.
PayPal Users Also Targeted Using Similar OAuth Exploits
Hackers are using the same strategy on platforms beyond Google. In March, attackers used a similar method to target PayPal users. They created fake email addresses through PayPal’s “gift address” feature and embedded phishing messages into the second address field.
PayPal then automatically sent a confirmation email to the attacker’s address. The attacker forwarded that message to a mailing list. Because the original email came from PayPal’s servers, it passed DKIM checks and looked official.
This trick works because email providers trust DKIM-verified messages. Attackers take advantage of that trust by forwarding real alerts to targets, using services like Google and PayPal to do the hard work for them.
BleepingComputer tested the PayPal attack and confirmed the method. They contacted PayPal, but the company did not respond to questions about the vulnerability.
Google First Denies, Then Confirms the Vulnerability
After Johnson identified the phishing method, he submitted a bug report to Google. At first, Google said the system was behaving as expected. But later, the company acknowledged that the issue could put users at risk.
Google is now working on a fix to close the loophole that allows attackers to spoof real alerts using OAuth-generated messages.
This vulnerability shows how email systems can be tricked by replayed DKIM signatures, especially when messages originate from trusted infrastructure. Email authentication systems like SPF, DKIM, and DMARC are important—but they can be bypassed if the message is forwarded after being signed.
Until Google completes the patch, the risk remains active.
Stay Safe From Google OAuth DKIM Replay Phishing Attacks
This phishing method is dangerous because the fake email passes all standard security checks. It uses Google’s own tools and domains. That makes it hard to detect.
To protect your Google account:
- Always double-check the domain name in any login link. Real Google login pages use accounts.google.com.
- Never enter your password into a site unless you are sure it’s the official Google login.
- Use two-factor authentication for extra security.
- Watch for emails that seem too urgent or suspicious—even if they pass DKIM and appear to come from Google.
- View full email headers if you’re suspicious. They may reveal mismatched “mailed-by” or “return-path” fields.
As attackers continue to find new ways to exploit trusted platforms, users need to stay alert and verify every detail. Even emails from no-reply@google.com can now be fake.
Stay Updated: Tech News